Whistleblower: Ubiquiti Breach “Catastrophic”

UPDATE (16/09/2022): The original source of this report has stated their source has since been indicted by federal prosecutors for his alleged wrongdoing – which includes providing false information to the press. It is likely that the information in this post is not fully accurate.
It has been reported that Ubiquiti have suffered a substantial breach of their systems.
On the 11th January, Ubiquiti reported that a breach involving a third-party cloud provider exposed customer account credentials.
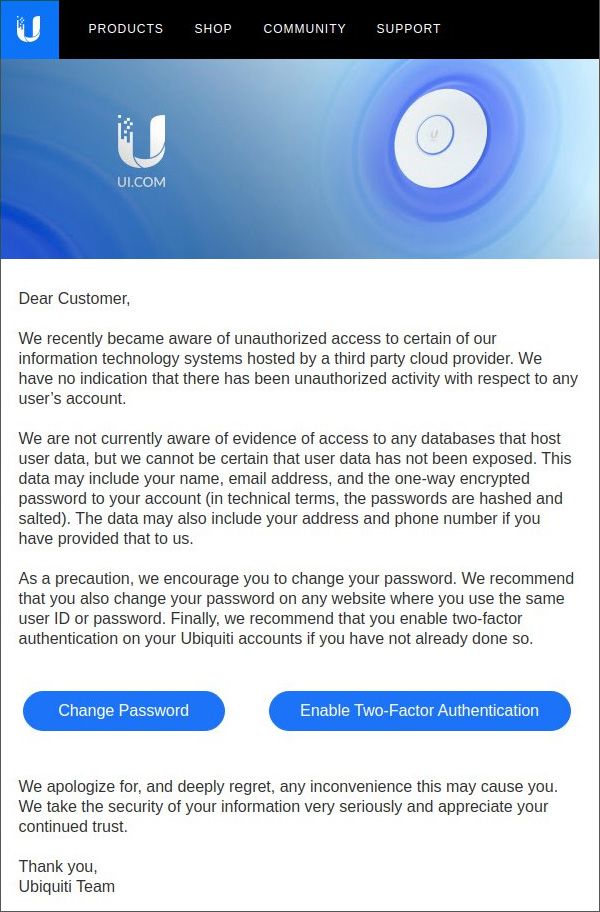
A source who participated in the response to that breach alleges Ubiquiti massively downplayed a “catastrophic” incident to minimize the hit to its stock price, and that the third-party cloud provider claim was a fabrication.
According to the source, the hackers obtained full read/write access to Ubiquiti databases at Amazon Web Services, which was the previously reported “third-party” involved in the breach.

The source has also disclosed that the attacker(s) had access to privileged credentials that were previously stored in the LastPass account of a Ubiquiti IT employee, and gained root administrator access to all Ubiquiti AWS accounts, including all S3 data buckets, all application logs, all databases, all user database credentials, and secrets required to forge single sign-on (SSO) cookies.
Essentially, any Ubiquiti cloud-based device could’ve been authenticated remotely all around the world.
Ubiquiti has shipped more than 85 million devices that play a key role in networking infrastructure in over 200 countries and territories worldwide.
“Ubiquiti had negligent logging (no access logging on databases) so it was unable to prove or disprove what they accessed, but the attacker targeted the credentials to the databases, and created Linux instances with networking connectivity to said databases”
Source:
