🛍️ UK Retail Under Siege: Cyber Attacks, Supply Chains & Lessons From M&S, Co-op, and Harrods

It’s been a turbulent fortnight for the UK’s retail sector — and not just because of late Easter deliveries or customer rows over the last Colin the Caterpillar. Three of the country’s most recognisable retail giants—Marks & Spencer, Co-op, and Harrods—have each faced cyber security incidents that disrupted operations, threatened supply chains, and triggered national investigations.
This isn’t coincidence, chaos, or clumsy coding. This is coordinated, targeted cyber activity exploiting long-known weaknesses in the retail ecosystem: flat networks, old infrastructure, third-party dependency, and sometimes a little too much optimism about the strength of perimeter defences.
Let’s break down what happened, what it means, and—most importantly—what needs to change.
🔍 The Retail Breach Rundown
🛒 Marks & Spencer: A Ransomware Wake-Up Call
Date: Mid-April
Impact:
- Click-and-collect & clothing orders suspended for nearly a week
- Manual tills and fridge monitoring in stores
- £3.8 million estimated daily revenue loss
- Market cap dropped £600 million
Threat Actor: Scattered Spider (known for sophisticated ransomware & extortion tactics)
Key Insight: The sheer operational fragility was exposed. One ransomware incident had cascading effects on everything from logistics to refrigeration. That’s not just bad luck—it’s a lack of segmentation and disaster planning.
M&S acted responsibly by shutting systems down and involving the Metropolitan Police, NCA and NCSC, but the long downtime suggests core systems were too interconnected to isolate safely.
BleepingComputer reported the hackers had stolen M&S data as early as February that could have helped them gain access to key systems.
🧾 Co-op: Virtual Desktops Go Dark & Member Info Stolen
Update: 2 May
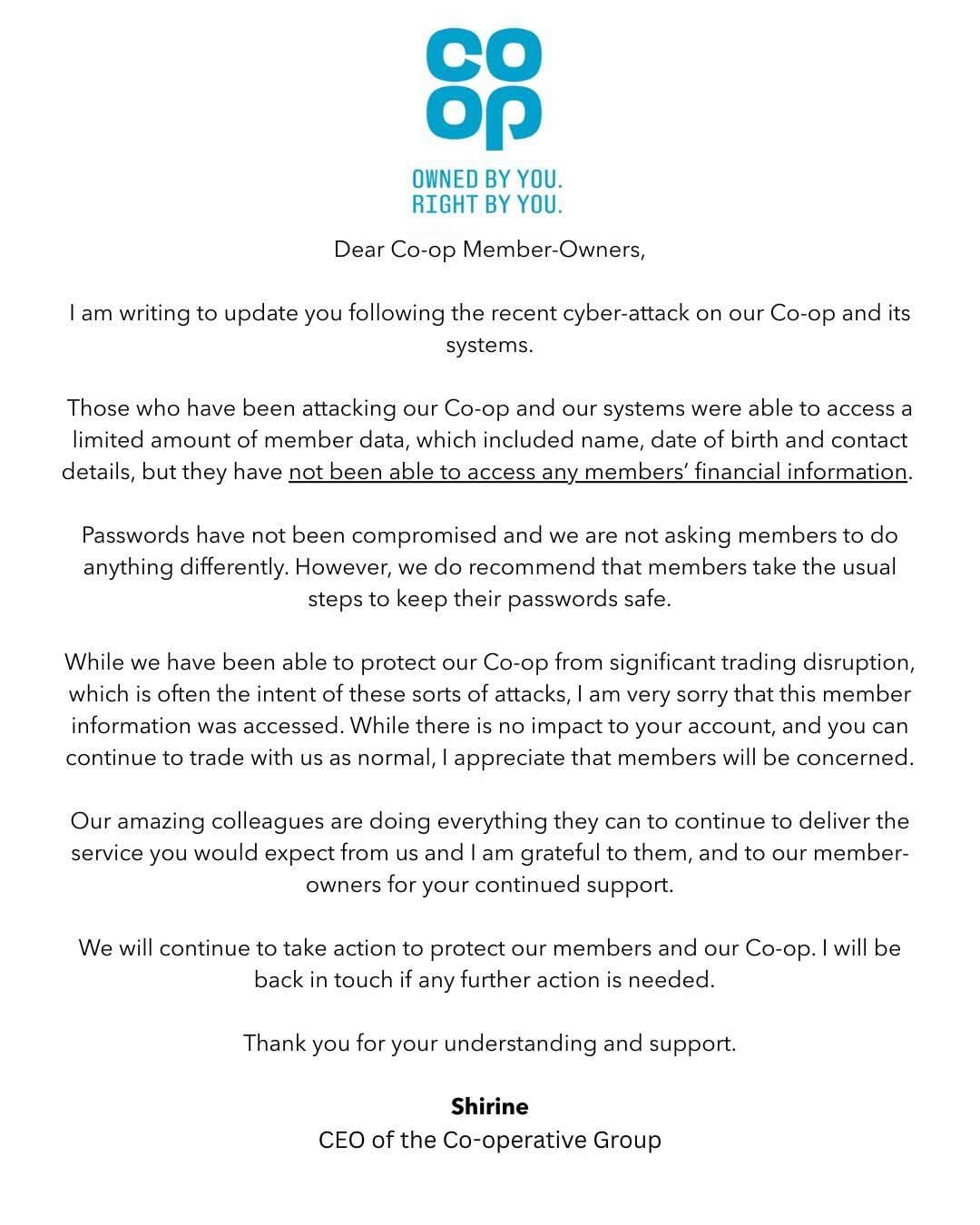
Date: 30 April
Impact:
- All remote access (VPN) to back-office systems has been shut down
- VDI (Virtual Desktop Infrastructure) fully suspended
- Stores and e-commerce remained operational
- Employees instructed not to enable transcripts on Teams meetings
- BBC Cyber security consultant Jen Ellis says the email implies that Co-op is worried about the presence of hackers (BBC, 2025).
Response: Fast action by Co-op IT to shut down systems likely prevented lateral movement.
Key Insight: When your VDI is your core workhorse, a breach here is like losing your company’s collective muscle memory. It points to risks in relying on single points of entry for operational access.
🎩 Harrods: The Luxury of Containment
Date: 1 May
Impact:
- Attempted unauthorised access
- Internal internet access suspended
- No disruption to stores or e-commerce
Response: Containment through segmentation—well played, Harrods. If only more firms could isolate networks that fast.
Key Insight: Harrods’ measured, quick response highlights the effectiveness of real-time segmentation and a proactive IT security function.
🧠 What’s Really Going On?
While each attack had different effects, they reflect a pattern of vulnerability across UK retail:
🎯 1. Attackers Are Hunting for Weakest Links
- Scattered Spider (M&S) uses social engineering, MFA bypasses, and ransomware payloads.
- Other groups (e.g., LockBit) often exploit public-facing services like RDP or steal credentials via phishing.
🔗 2. Supply Chains Are the Quiet Backdoors
- Third-party vendors (e.g., logistics, SaaS platforms) often have excessive access.
- Past cases like the Blue Yonder breach show attackers gaining access via partners with poor cyber hygiene.
🧱 3. Legacy Systems Are Still Everywhere
- Retailers often rely on outdated POS systems and monolithic ERP setups with flat network architectures.
- Once attackers gain a foothold, lateral movement is just a matter of time.
🛡️ The NCSC Steps In: “Prepare, Respond, Recover”
Following these incidents, the National Cyber Security Centre (NCSC) issued targeted guidance for UK retailers. It’s one of the more practical and direct advisories in recent memory—well worth reading in full here. Key highlights include:
🔐 1. Zero Trust Everything
- Segregate networks: POS, corporate, and e-commerce must not share the same playground.
- MFA isn't optional—it's your cyber hygiene basic.
🧰 2. Incident Response Is a Muscle — Train It
- Have automated playbooks and test them like fire drills.
- Engage a Cyber Incident Response (CIR) provider before the breach, not after.
🔍 3. Monitor Like You Mean It
- Use User and Entity Behaviour Analytics (UEBA) and Intrusion Detection to catch anomalies.
- Leverage dark web monitoring tools to detect leaked credentials or internal chatter.
🚚 4. Audit Your Supply Chain Like It's Part of Your Network
- Demand security certifications (SOC 2 Type II, ISO 27001) from vendors.
- Secure code pipelines with code signing and update verification.
📊 Drawing Conclusions: M&S as a Case Study
Among the three, M&S provides the clearest insight into the real-world impact of cyber compromise:
| Category | Impact |
|---|---|
| Daily Revenue Loss | £3.8 million |
| Stock Market Drop | £600 million |
| Outage Duration | ~6 days |
| Manual Interventions | Tills & fridge monitoring |
| Response Team | NCSC, NCA, Met Police |
Conclusion: Without segmentation and resilient architecture, even a single breach can disrupt logistics, sales, and brand trust across the board. This wasn't just an IT problem—it was a business continuity failure.
🧭 Final Thoughts: The Path Forward
The past two weeks have shown us that UK retailers are attractive, accessible, and under-prepared. But they’ve also shown us what works: fast containment (Harrods), proactive response (Co-op), and full transparency (M&S).
Here’s your TL;DR if you’re short on time and high on risk:
- Plan for ransomware like it’s already in your inbox.
- Treat your suppliers like they’re part of your attack surface—because they are.
- Build networks that fail gracefully, not catastrophically.
- If your response plan is on a SharePoint page last updated in 2019, it’s not a plan—it’s a liability.
Cyber threats in retail aren’t going anywhere. But with the right tools, practices, and a little humility (plus a solid backup plan for the fridges), we can make these stories rarer and the recovery faster.
Stay patched. Stay vigilant. And yes, keep an eye on Percy Pig—he might just be next.