Deconstructing HTTP/2 Rapid Reset Attack (CVE-2023-44487)
Over the last few days, you might have heard about the 'rapid reset' vulnerability in the HTTP/2 protocol (known as CVE-2023-44487).
This post will break it down into a few sections, including how it works, the scale of the problem, and how fixes are being implemented.
Amazon Web Services, Cloudflare, and Google, have already announced their experiences of this vulnerability, and how it was detected, and what they are doing / have done to protect their clients' assets from this attack. Some providers detected this vulnerabiltiy as early as the 25th August 2023.
What is this vulnerability?
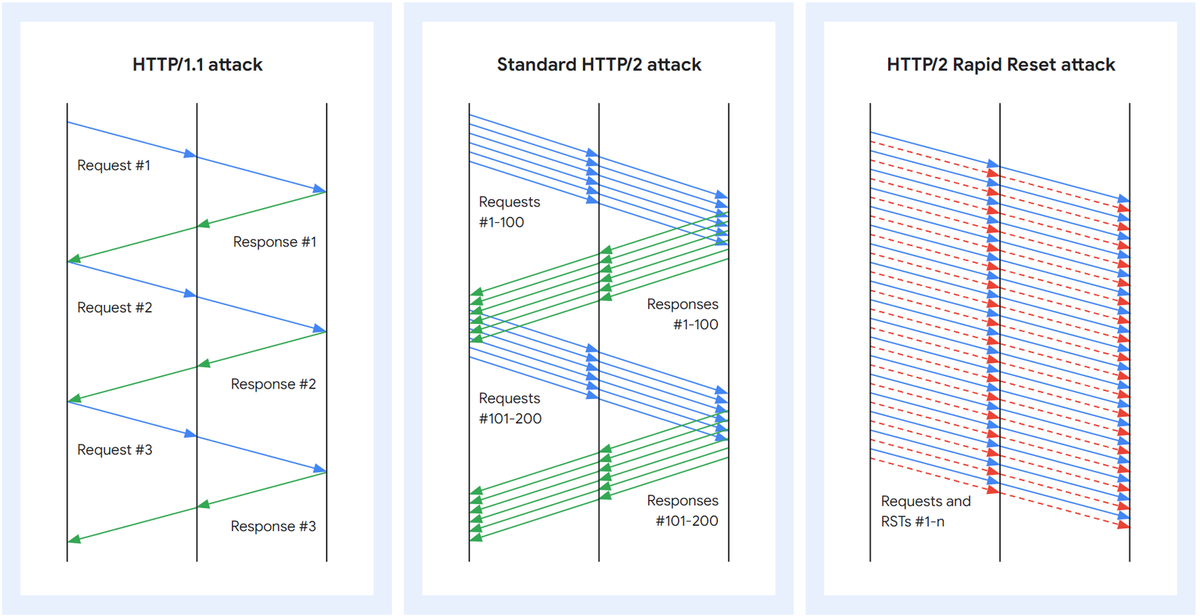
In HTTP/1.1, each request is processed sequentially. The server will read a request, process it, compose a response, and ONLY then, read and process the next request.
The 'Rapid Reset' technique exploits a feature of HTTP/2, called 'stream multiplexing'. Stream multiplexing is great because it enables clients to have multiple in-transition requests without the need for many individual connections, reducing round-trip times compared to the previous HTTP/1.1 version.
In essence, a large number of requests followed by swift cancellations can impose a significant workload on the server, all while incurring minimal costs for the attacker, essentially giving attackers with limited resources the ability to perform extremely powerful Denial of Service attacks.
A quote from Cloudflare:
"The attacker was able to generate such an attack with a botnet of merely 20,000 machines. There are botnets today that are made up of hundreds of thousands or millions of machines. Given that the entire web typically sees only between 1–3 billion requests per second, it's not inconceivable that using this method could focus an entire web’s worth of requests on a small number of targets."
This vulnerability has actually broken records by far, with some attacks detected at over 201 million requests per second, which is over 3x bigger than an attack mitigated by Cloudflare in February this year (2023), of over 71 million requests per second.
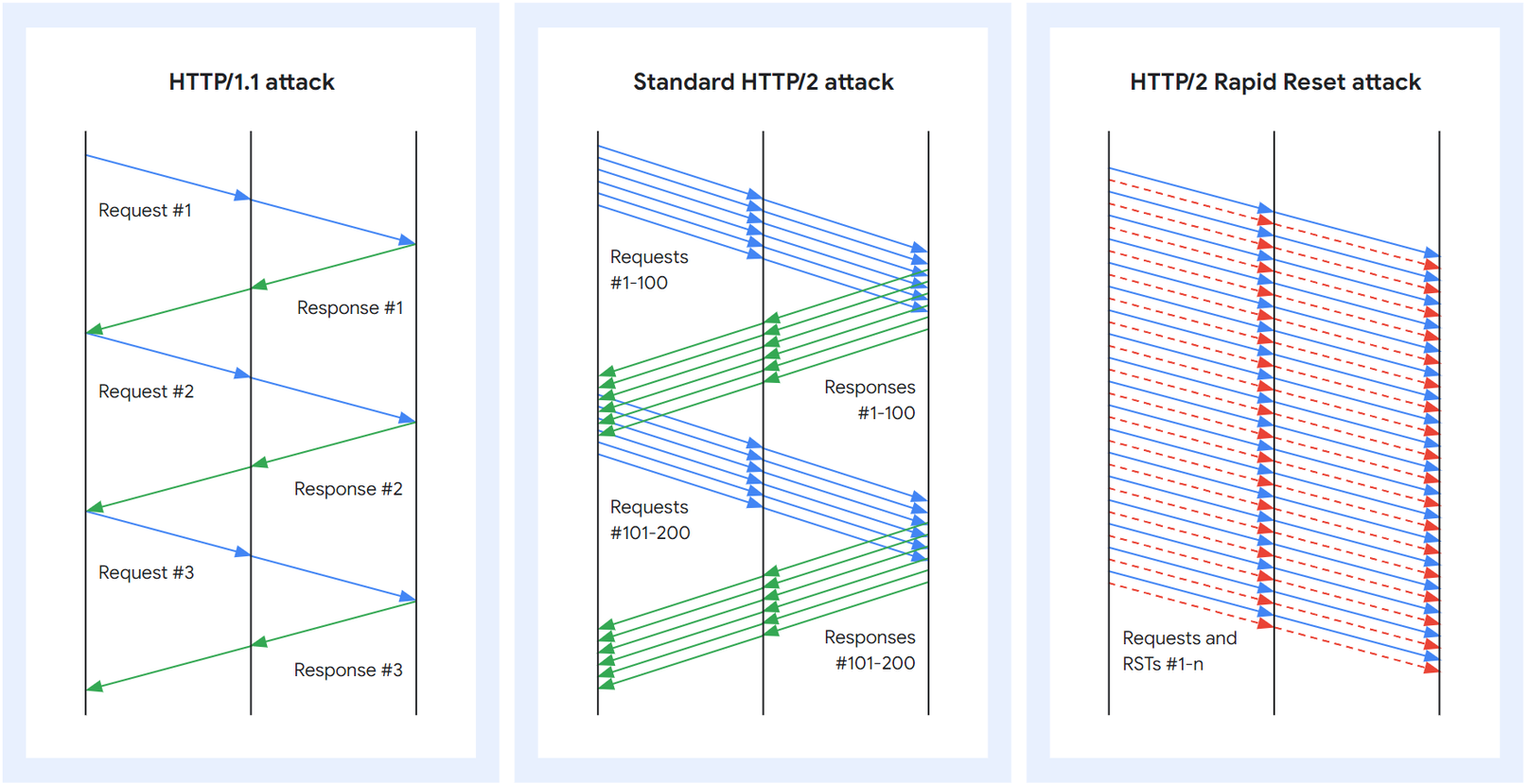
HTTP/2 does include a security feature aimed at restricting the number of active streams to safeguard against DoS attacks. However, this safeguard clearly isn't foolproof. The protocol permits clients to unilaterally cancel streams, and this vulnerability is exploited in the attack. Botnets are capable of generating an extensive volume of requests, thereby posing a significant threat to the web infrastructures they target.
How is it being fixed?
Most Big Tech platforms have all implemented patches for their service clients. If you are self-hosted, it is important to implement patches as soon as possible.
Nginx released a patch for their web server software today, which is actually an incredibly simple fix, with a total of 17 lines modified:
.
Apache has also rolled out patches for its various software platforms, including Traffic Server:
As always, keep your software/security patches up-to-date as soon as possible! Stay safe out there!
Helpful References/Resources
- https://github.com/dotnet/core/blob/e4613450ea0da7fd2fc6b61dfb2c1c1dec1ce9ec/release-notes/6.0/6.0.23/6.0.23.md?plain=1#L73
- https://blog.cloudflare.com/technical-breakdown-http2-rapid-reset-ddos-attack/
- https://aws.amazon.com/security/security-bulletins/AWS-2023-011/
- https://cloud.google.com/blog/products/identity-security/how-it-works-the-novel-http2-rapid-reset-ddos-attack
- https://www.nginx.com/blog/http-2-rapid-reset-attack-impacting-f5-nginx-products/
- https://cloud.google.com/blog/products/identity-security/google-cloud-mitigated-largest-ddos-attack-peaking-above-398-million-rps/
- https://news.ycombinator.com/item?id=37831062
- https://blog.cloudflare.com/zero-day-rapid-reset-http2-record-breaking-ddos-attack/
- https://www.phoronix.com/news/HTTP2-Rapid-Reset-Attack
- https://github.com/envoyproxy/envoy/pull/30055
- https://github.com/haproxy/haproxy/issues/2312
- https://github.com/eclipse/jetty.project/issues/10679
- https://forums.swift.org/t/swift-nio-http2-security-update-cve-2023-44487-http-2-dos/67764
- https://github.com/nghttp2/nghttp2/pull/1961
- https://github.com/netty/netty/commit/58f75f665aa81a8cbcf6ffa74820042a285c5e61
- https://github.com/alibaba/tengine/issues/1872
- https://github.com/apache/tomcat/tree/main/java/org/apache/coyote/http2
- https://news.ycombinator.com/item?id=37830987
- https://news.ycombinator.com/item?id=37830998
- https://github.com/caddyserver/caddy/issues/5877
- https://www.bleepingcomputer.com/news/security/new-http-2-rapid-reset-zero-day-attack-breaks-ddos-records/
- https://github.com/bcdannyboy/CVE-2023-44487
- https://github.com/grpc/grpc-go/pull/6703
- https://github.com/icing/mod_h2/blob/0a864782af0a942aa2ad4ed960a6b32cd35bcf0a/mod_http2/README.md?plain=1#L239-L244
- https://github.com/nghttp2/nghttp2/releases/tag/v1.57.0
- https://mailman.nginx.org/pipermail/nginx-devel/2023-October/S36Q5HBXR7CAIMPLLPRSSSYR4PCMWILK.html
- https://my.f5.com/manage/s/article/K000137106
- https://msrc.microsoft.com/blog/2023/10/microsoft-response-to-distributed-denial-of-service-ddos-attacks-against-http/2/
- https://bugzilla.proxmox.com/show_bug.cgi?id=4988
- https://cgit.freebsd.org/ports/commit/?id=c64c329c2c1752f46b73e3e6ce9f4329be6629f9
- https://seanmonstar.com/post/730794151136935936/hyper-http2-rapid-reset-unaffected
- https://github.com/microsoft/CBL-Mariner/pull/6381
- https://groups.google.com/g/golang-announce/c/iNNxDTCjZvo
- https://github.com/facebook/proxygen/pull/466
- https://gist.github.com/adulau/7c2bfb8e9cdbe4b35a5e131c66a0c088
- https://github.com/micrictor/http2-rst-stream
- https://edg.io/lp/blog/resets-leaks-ddos-and-the-tale-of-a-hidden-cve
- https://openssf.org/blog/2023/10/10/http-2-rapid-reset-vulnerability-highlights-need-for-rapid-response/
- https://github.com/h2o/h2o/security/advisories/GHSA-2m7v-gc89-fjqf
- https://github.com/h2o/h2o/pull/3291
- https://github.com/nodejs/node/pull/50121
- https://github.com/dotnet/announcements/issues/277
- https://github.com/golang/go/issues/63417
- https://github.com/advisories/GHSA-vx74-f528-fxqg
- https://github.com/apache/trafficserver/pull/10564
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-44487
- https://tomcat.apache.org/security-10.html#Fixed_in_Apache_Tomcat_10.1.14
- https://lists.apache.org/thread/5py8h42mxfsn8l1wy6o41xwhsjlsd87q
- https://www.openwall.com/lists/oss-security/2023/10/10/6
- https://www.haproxy.com/blog/haproxy-is-not-affected-by-the-http-2-rapid-reset-attack-cve-2023-44487
- https://github.com/opensearch-project/data-prepper/issues/3474
- https://github.com/kubernetes/kubernetes/pull/121120
- https://github.com/oqtane/oqtane.framework/discussions/3367
- https://github.com/advisories/GHSA-xpw8-rcwv-8f8p
- https://netty.io/news/2023/10/10/4-1-100-Final.html
- https://www.cisa.gov/news-events/alerts/2023/10/10/http2-rapid-reset-vulnerability-cve-2023-44487
- https://www.theregister.com/2023/10/10/http2_rapid_reset_zeroday/
- https://blog.qualys.com/vulnerabilities-threat-research/2023/10/10/cve-2023-44487-http-2-rapid-reset-attack
- https://news.ycombinator.com/item?id=37837043
- https://github.com/kazu-yamamoto/http2/issues/93
- https://martinthomson.github.io/h2-stream-limits/draft-thomson-httpbis-h2-stream-limits.html
- https://github.com/kazu-yamamoto/http2/commit/f61d41a502bd0f60eb24e1ce14edc7b6df6722a1
- https://github.com/apache/httpd/blob/afcdbeebbff4b0c50ea26cdd16e178c0d1f24152/modules/http2/h2_mplx.c#L1101-L1113
- debian.org: DSA-5522 (vendor advisory)
- debian.org: DSA-5521 (vendor advisory)