Decompiling Zac Alsop's 'I Challenged A Hacker To Ruin My Life In 30 Days' Video

I've been a long-time viewer of Zac's channel and recently enjoyed his 'I Challenged A Hacker To Ruin My Life In 30 Days' video - a true insight into how some of the bad actors in our society can commit harrowing crimes to the otherwise unsuspecting individual/organisation.
If you haven't watched the video, I highly recommend you do so! In short, he challenges both Tony Sales - previously famously known as 'Britain's greatest fraudster', and Solomon Gilbert - former cyber criminal, to commit various acts in order to steal his identity and hack his digital property. It gives people a good insight into what could happen, and does happen, across the world.
Naturally, the cyber security engineer in me wanted to decompile all the individual situations in his video, describing how each element works, and how to protect yourself from these attacks yourself. So, spoiler alert if you haven't watched the video already.
Their Action Plan

In order to gain 100% digital replication of Zac's information to steal his identity, Tony and Solomon (I will refer to them as T&S from now on) used a variety of methods.
Act 1 - OSINT (Open Source Intelligence)

What happened?
T&S discussed how, due to the nature of Zac's job, he is already 'quite public', and listed all of his public social media accounts, including Twitter, Instagram, YouTube and LinkedIn.
S immediately mentioned that Zac's LinkedIn is more 'geared towards professionals', and the fact Zac talks 'a little bit more about his own life' - and already highlights that there would be more OSINT to gather from here.
How can I protect myself from OSINT?
Zac was certainly at a bigger disadvantage here, given the fact his job is a public-facing one. There are thousands of pictures, videos, and metadata of Zac across the internet, which makes it easier for threat actors to gather open intelligence on him.
Always be extremely careful with what information about yourself is freely available to anyone online. Check your online profiles, and manage privacy settings on social media. Who do you accept friend requests from? Do you delete metadata from photos before uploading?
Act 2 - Dumpster Diving

What happened?
T heads over to Zac's office location at 3AM to go dumpster diving in the large waste bins. In order to blend in, T wears a Just Eat orange coat, given that Z's office building is near a resturant. He collects 8 sacks of rubbish, and takes them back to HQ, where he found lots of sensitive information. To be exact, 12x email addresses, 4x phone numbers, 5x physical addresses, and 1x bank statement.
How can I protect myself from dumpster diving?
Well, I'm sure the answer is quite obvious here. Don't dispose of sensitive information without destroying it beyond all recognition beforehand. Use a paper shredder, burn it, etc. The more pieces of the puzzle you give the threat actors, the easier it is for them to make up the rest.
Act 3 - WiFi hijacking (Pineapple)
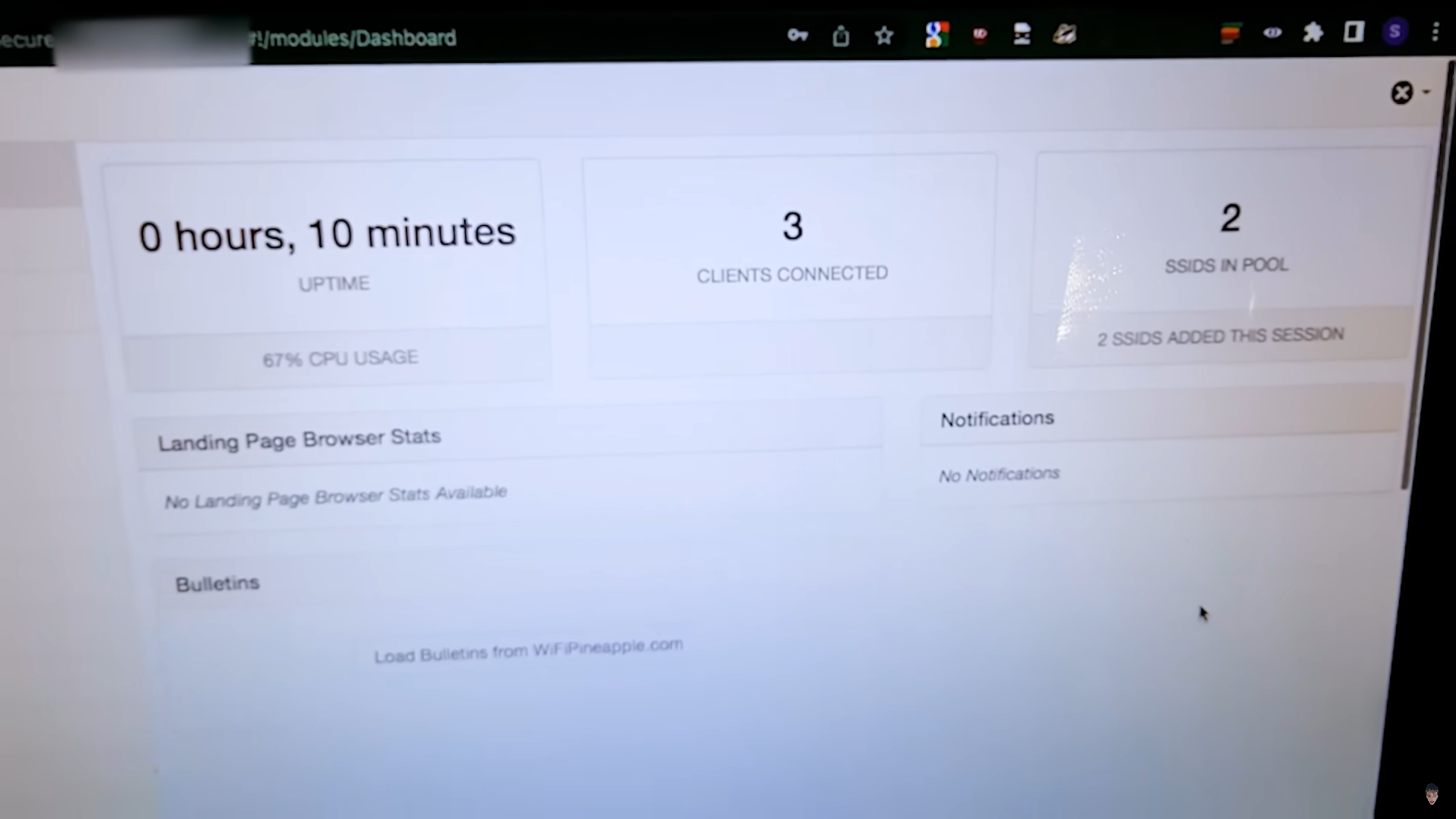
What happened?
S deployed a WiFi Pineapple outside Zac's office. This is a portable device that enables cyber criminals to immitate data shared on WiFi networks. In this case, tricking Z's client devices (phones, laptops, printers, etc) to connect to the Pineapple rather than his real Access Point (or router).
After 10 minutes, 3 of Zac's devices connected to the pineapple. S then uses DNS Redirection to a fake web server to immitate websites including Instagram, YouTube, and after a few days, his National Insurance number.
This is a common attack, sometimes called man-in-the-middle 'Evil Portal' attack. The unsuspecting user thinks they are connecting to the real website, and enters their usual data (such as a username and password to login), and this information goes straight to the threat actor, before reaching the real destination server.
How can I protect myself from WiFi Pineapple attacks?
- Use Strong Passwords: Secure your Wi-Fi network with a strong, unique password. Avoid using default or easily guessable passwords.
- Don't use obvious SSIDs: Aim to use an SSID that doesn't identify you as the target. For example, "Johns Watch Shop" is a dead giveaway of who the network belongs to.
- Enable WPA2 or WPA3 Encryption: Use the latest and strongest encryption protocol available on your router. WPA2 and WPA3 are more secure than WEP or open networks.
- Disable WPS: Wi-Fi Protected Setup (WPS) can be exploited by attackers. Disable it in your router settings.
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic, making it more difficult for attackers to intercept your data. Use a reputable VPN service, especially when connecting to public Wi-Fi networks.
- Stay Updated: Keep your router's firmware and all connected devices updated with the latest security patches. Manufacturers often release updates to fix vulnerabilities.
- Verify Network Names (SSIDs): Be cautious when connecting to open or unfamiliar networks. Ensure you're connecting to the correct network by verifying the SSID with the network owner.
- Turn Off Auto-Connect: Disable auto-connect features on your devices, which might automatically connect to open or known networks without your consent.
- Forget Unnecessary Networks: Remove saved Wi-Fi networks that you no longer use or trust from your device's list of known networks.
- Use a Mobile Hotspot: When in doubt about the security of a public Wi-Fi network, consider using your smartphone as a mobile hotspot instead.
- Monitor for Suspicious Activity: Regularly check the devices connected to your network and router logs for any unusual activity.
- Use HTTPS: Whenever possible, use websites and services that employ HTTPS encryption. This ensures that your data is encrypted in transit.
- Implement MAC Address Filtering: This allows you to specify which devices are allowed to connect to your network based on their MAC addresses. While it's not foolproof (MAC addresses can be spoofed), it adds an extra layer of security.
- Enable Intrusion Detection: Some routers have intrusion detection features that can help detect rogue access points or suspicious activity on your network.
- Use a Wireless Intrusion Prevention System (WIPS): WIPS solutions can help detect and prevent unauthorized access points and attacks on your Wi-Fi network.
- Physical Security: Secure your router in a physically safe location to prevent unauthorized access or tampering.
Remember that no security measure is entirely foolproof, but by implementing these precautions, you can significantly reduce the risk of falling victim to WiFi Pineapple attacks and other similar threats.
Act 4 - Data Theft via Physical Break-in

What happened?
T&S broke into Zac's office after surveilling to ensure he was not in. After breaking in, they found lots of information lying about, including his phone number, business bank details, addresses and WiFi passwords written on the wall.
How can I protect myself from data theft via physical break-in?
It's crucial to safeguard sensitive information, a few steps you could take to enhance data security in these situations:
- Physical Security Measures:
- Access Control: Implement strong access control measures, including key cards, biometric authentication, or security guards to restrict entry to your office.
- Surveillance Cameras: Install security cameras in and around your office to monitor and record any suspicious activities.
- Alarms: Invest in a reliable alarm system that can notify authorities and employees in case of a break-in.
- Secure Entrances: Ensure that entrances and windows are reinforced with strong locks, bars, and shatter-resistant glass.
- Safe Room: Designate a secure room within the office where critical data and equipment can be stored during emergencies.
- Data Encryption:
- Encrypt sensitive data on your computers, servers, and mobile devices. Even if thieves steal the hardware, the data will remain unreadable without the encryption key.
- Data Backup and Offsite Storage:
- Regularly back up all critical data and store backups in an offsite location. This ensures that your data can be restored even if physical equipment is stolen or damaged.
- Remote Data Wiping:
- Implement remote data wiping capabilities for mobile devices and laptops. This allows you to erase sensitive data on stolen devices to prevent unauthorized access.
- Server Room Security:
- If your office has a server room, ensure it is well-secured with restricted access, surveillance, and environmental controls (e.g., fire suppression systems).
- Data Classification:
- Classify your data based on its sensitivity and importance. Apply stronger security measures to highly sensitive information.
- Employee Training:
- Train your employees on security protocols and the importance of physical security. Encourage them to lock their workstations and secure portable devices when not in use.
- Visitor Logs:
- Keep a log of all visitors to your office. Require them to sign in and out, and escort them while they are on the premises.
- Inventory Management:
- Maintain an inventory of all office equipment and IT assets. This can help with tracking and reporting stolen items.
- Incident Response Plan:
- Develop a comprehensive incident response plan that outlines what to do in case of a physical break-in. Assign roles and responsibilities, and practice drills with your staff.
- Insurance:
- Consider insurance policies that cover theft, property damage, and data breaches. Review your coverage to ensure it meets your needs.
- Legal and Regulatory Compliance:
- Comply with data protection laws and regulations that apply to your industry. Failure to do so may result in legal consequences if data is compromised.
- Document Destruction:
- Properly dispose of sensitive paper documents through shredding or other secure methods. Don't leave documents with sensitive information lying around.
- Vendor Security:
- Assess the physical security measures of third-party vendors who have access to your office, especially if they handle sensitive data.
By implementing these measures, you can significantly reduce the risk of data breaches and minimise the impact of a physical break-in on your business operations. Regularly review and update your security protocols to adapt to evolving threats and technologies.
Act 5 - Developed a Deepfake to open a Digital Bank Account & take out a loan
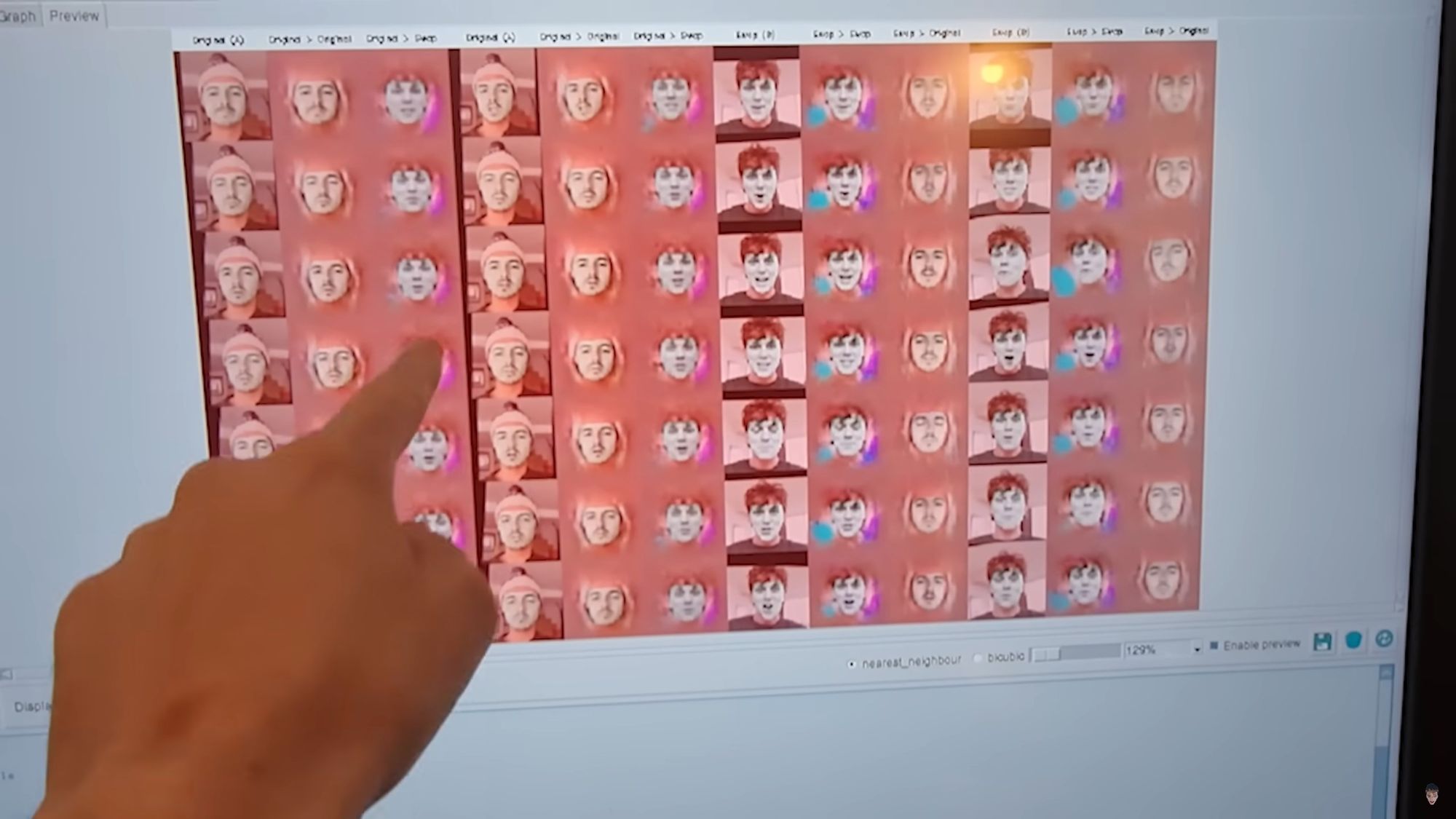
What happened?
Using Deepfake technology, S managed to superficially morph his face to Zac's, meaning he was able to create a live deepfake to setup a digital bank account under Zac's name.
How can I protect myself from Deepfake Technology?
Preventing someone from stealing your face data to create deepfakes for fraudulent activities like opening digital bank accounts requires vigilance and proactive measures. Here are some steps you can take to protect your face data:
- Limit Exposure:
- Be cautious about sharing personal photos and videos on social media and other public platforms. Limit the amount of personal information available online.
- Privacy Settings:
- Adjust the privacy settings on your social media accounts to restrict access to your photos and personal information. Only allow people you trust to view your content.
- Two-Factor Authentication (2FA):
- Enable 2FA on your online accounts, especially those related to financial institutions. This adds an extra layer of security, making it harder for fraudsters to access your accounts.
- Secure Your Devices:
- Use strong, unique passwords or passcodes to lock your devices (smartphones, tablets, computers). Enable biometric authentication like fingerprint or facial recognition if available.
- Be Cautious with Selfies:
- Be careful when taking selfies or photos with your face clearly visible. Avoid taking pictures that could be used to create deepfakes, such as close-up shots with various facial expressions.
- Regularly Review Accounts:
- Regularly check your bank and financial statements for any suspicious activity. Report any unauthorized transactions immediately.
- Email Security:
- Be cautious about opening emails or clicking on links from unknown sources. Phishing emails may lead to data breaches.
- Use Trusted Services:
- When using online services or apps, ensure they are from reputable sources and have strong security measures in place.
- Report Suspicious Activity:
- If you suspect that someone is using your face data for fraudulent purposes, report it to the relevant authorities and financial institutions immediately.
- Educate Yourself:
- Stay informed about deepfake technology and emerging threats. Knowledge can help you recognize potential risks.
- Secure Your Data:
- Regularly back up your important data and enable encryption on your devices to protect data in case of theft.
- Biometric Locks:
- Some smartphones and laptops offer biometric locks that can be used to secure your device and data. Use them if available.
- Avoid Public Wi-Fi:
- Be cautious when connecting to public Wi-Fi networks, as they may not be secure. Use a virtual private network (VPN) for added security when accessing sensitive information.
- Request Verification:
- Some social media platforms offer account verification features. If you have a significant online presence, consider requesting verification to reduce the risk of impersonation.
Remember that while these steps can help mitigate the risk of your face data being used for fraudulent activities, no system is entirely foolproof. Being vigilant and proactive is your best defense against such threats.
Act 6 - Withdrew cash & bought Bitcoin in Foreign Country
What happened?
T withdrew cash from the account they created in Zac's name (using his money), and used this cash to purchase bitcoin in a foreign country, which they then used to buy property in Zac's name.
This is really linked to all the previous acts above - this is just the final straw!
Conclusions
In conclusion, Zac's eye-opening video serves as a stark reminder of the ever-present threats in the digital age. The actions of the hackers, Tony Sales and Solomon Gilbert, highlighted the various vulnerabilities that individuals and organisations can face, as well as the importance of cybersecurity awareness and proactive measures to protect oneself from such attacks.
Throughout the video, we witnessed a series of meticulously planned and executed attacks, each with its own lessons and precautions. From open-source intelligence gathering to dumpster diving, WiFi hijacking, physical break-ins, deepfake technology, and financial manipulation, the hackers demonstrated the breadth of tactics employed by malicious actors in our interconnected world.
The critical takeaway from these acts is the importance of personal and organisational vigilance. Protecting sensitive information, managing online presence, and implementing robust security measures are essential steps in safeguarding against potential threats.
Whether it's securing your digital footprint, fortifying your physical environment, or staying informed about emerging technologies like deepfakes, staying proactive is key.
While no defense can be completely foolproof, the combination of knowledge, awareness, and practical precautions can significantly reduce the risk of falling victim to cybercrimes. Zac's video serves as a valuable educational resource, reminding us that in the digital age, the responsibility of safeguarding our personal and professional lives falls largely on our shoulders.
It's a call to action for all of us to take cybersecurity seriously, protecting ourselves and our digital assets from the ever-evolving threat landscape.
As always – stay safe out there!