Defence in Depth & The Wet Bandits
Intro
I've been asked by friends and colleagues a lot about this "defence in depth" topic; usually something along the lines of "what exactly does defence in depth mean?"

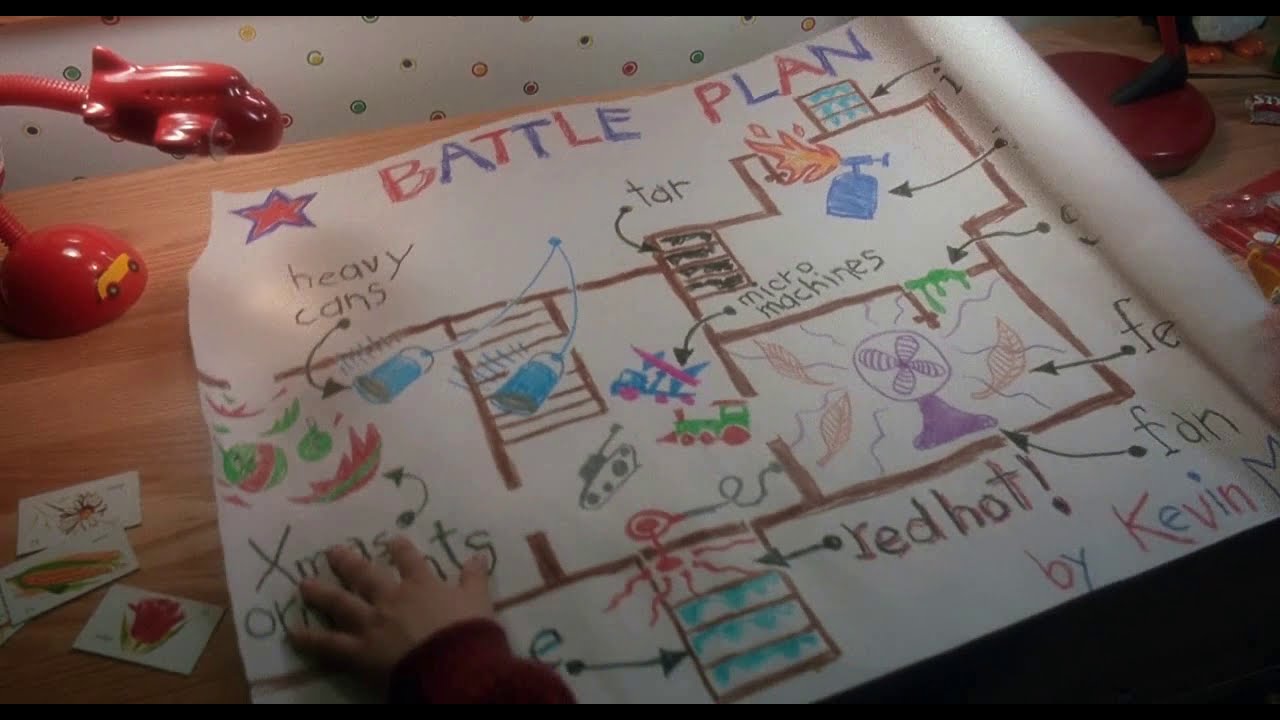
Typically, I'd show them something like the above image and say "well, kind of the opposite of that?"
"Yeah I get it - what does it really mean?"
Well, the ‘official’ definition of Defence in Depth is as follows: "Defense in depth is a concept used in information security in which multiple layers of security controls (defense) are placed throughout an information technology (IT) system. Its intent is to provide redundancy in the event a security control fails or a vulnerability is exploited that can cover aspects of personnel, procedural, technical and physical security for the duration of the system's life cycle." Defense in depth (computing) - Wikipedia (2022)
The topic is vast, especially to beginners, so I thought about a better way to explain it to peers without it sounding confusing and overwhelming. I didn't know where to begin. It wasn't until I was watching Home Alone that it hit me... Kevin McCallister is the MASTER of Defence in Depth! Okay, maybe not specifically in cyber security, but he's helped form the perfect analogy for me... BATTLE PLAN!
Battle Plan
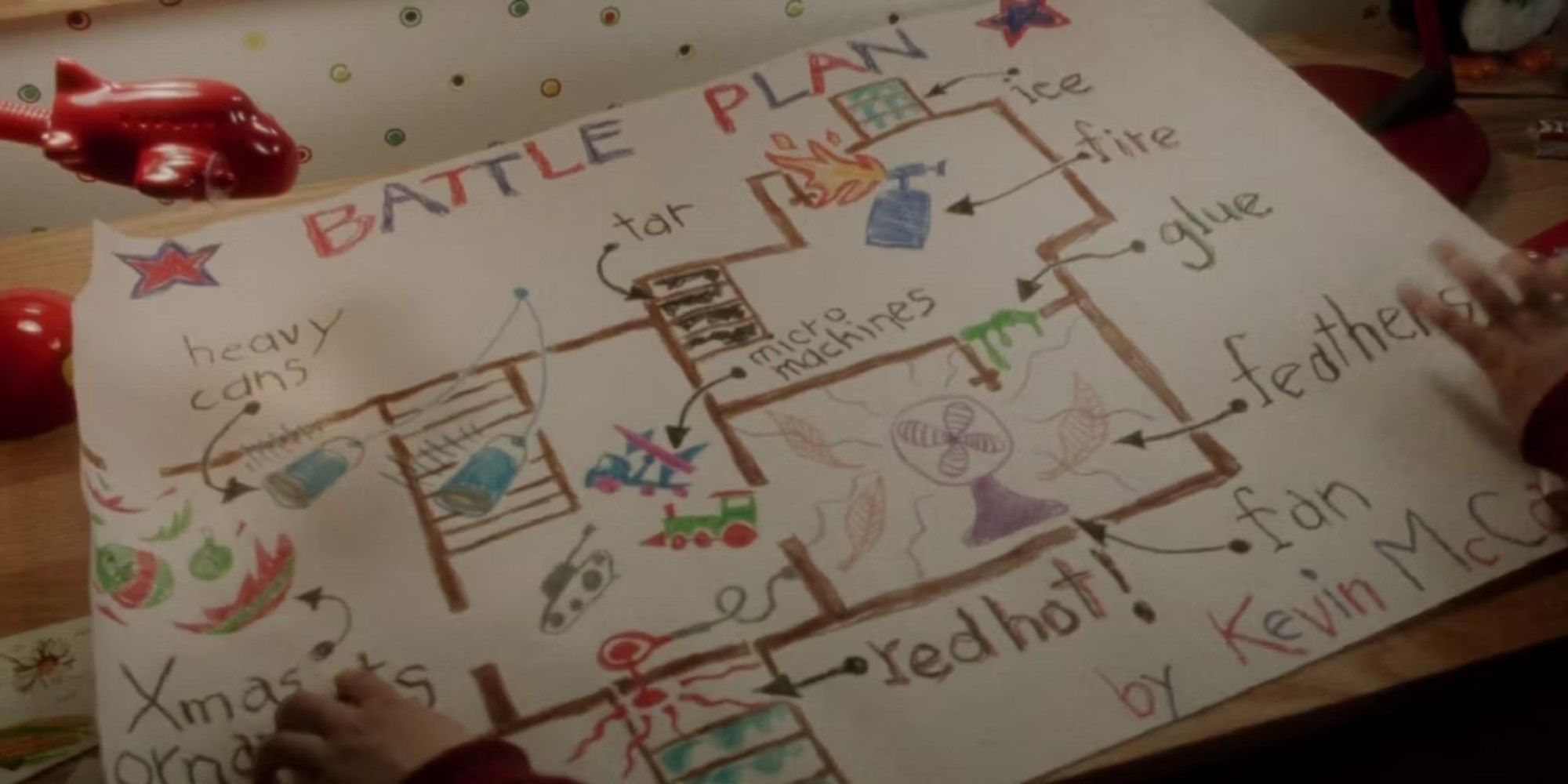
The world can be a nasty place, and the internet connects the world together. It can be an incredibly useful tool for organisations and businesses but a zero-trust policy should always be put in place, and, in the current climate, a “battle plan” for not if but when an attacker attempts to get into your systems – in order to minimise damage and protect data.
In Home Alone, Kevin does not assume that everything is safe if he keeps the bad guys outside. Instead, he assumes they WILL get in and has multiple defence mechanisms ready for them when they do.
If a person or organisation does not have a sufficient 'battle plan' in place, it puts their systems at huge risk. Aside from the legal and regulatory risk assessments, a full in-depth layered defence in depth structure should be adopted as standard. It is through the layering of multiple defence techniques that Kevin can protect his house from thieves (aka The soon-to-become Wet Bandits). That is exactly how you should think about your own security measures.
Layered Security Measures
SCENARIO: Harry and Marv (pictured) have taken up Black Hat Hacking but are also avid fluffy cat and dog lovers. They are trying to attack your mission critical assets (in this case, your cute fluffy cat and dog pictures) to sell on the web to make a quick buck. They have found your IP Address because you visited their malicious website (catsanddogs.totallynotamaliciouswebsite.com) without using a VPN or a secure browser and now they’re coming for your pics. Lucky for you, your security measures have been configured and layered at every point in your infrastructure. The chances of your pics getting accessed are slim!
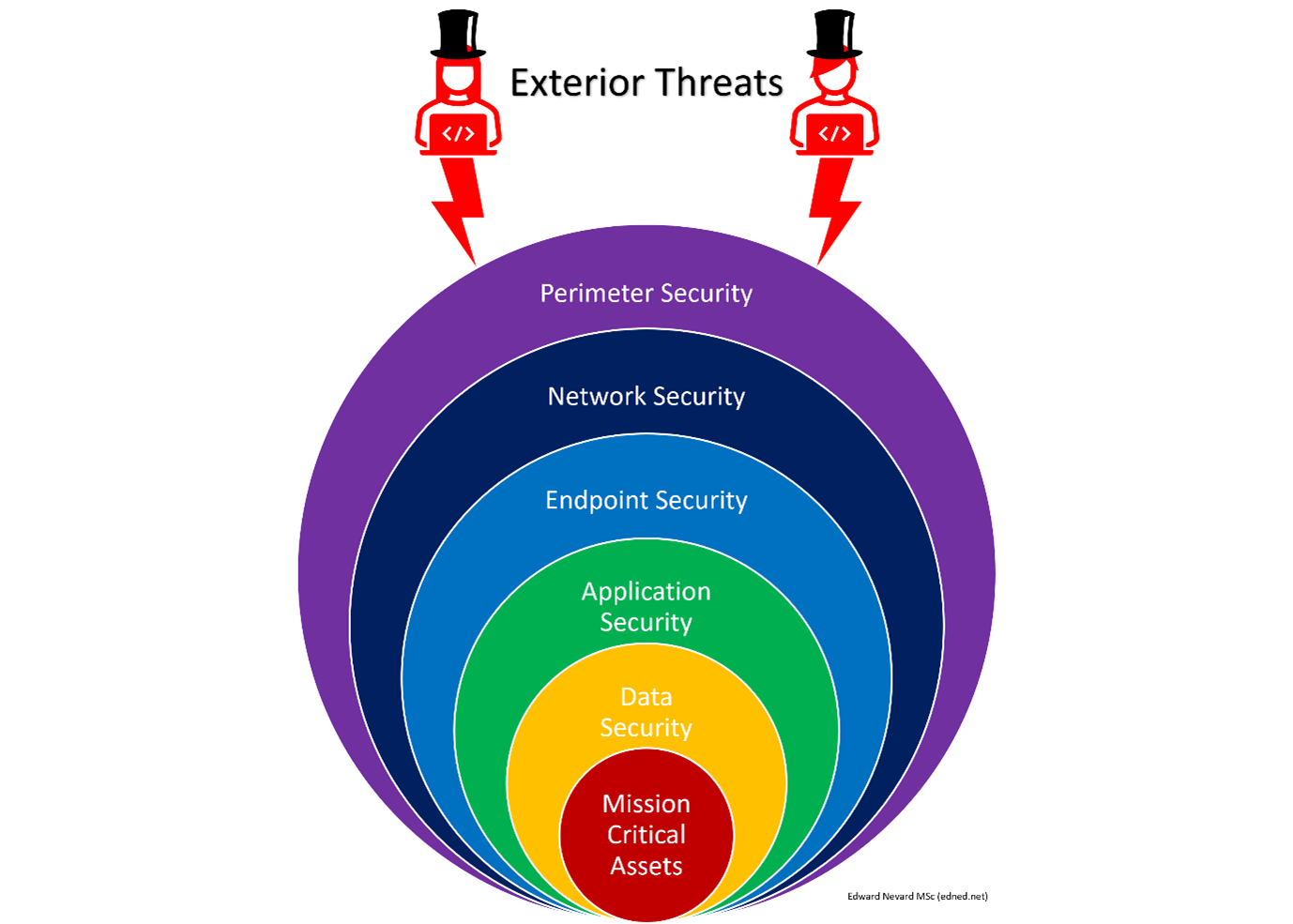
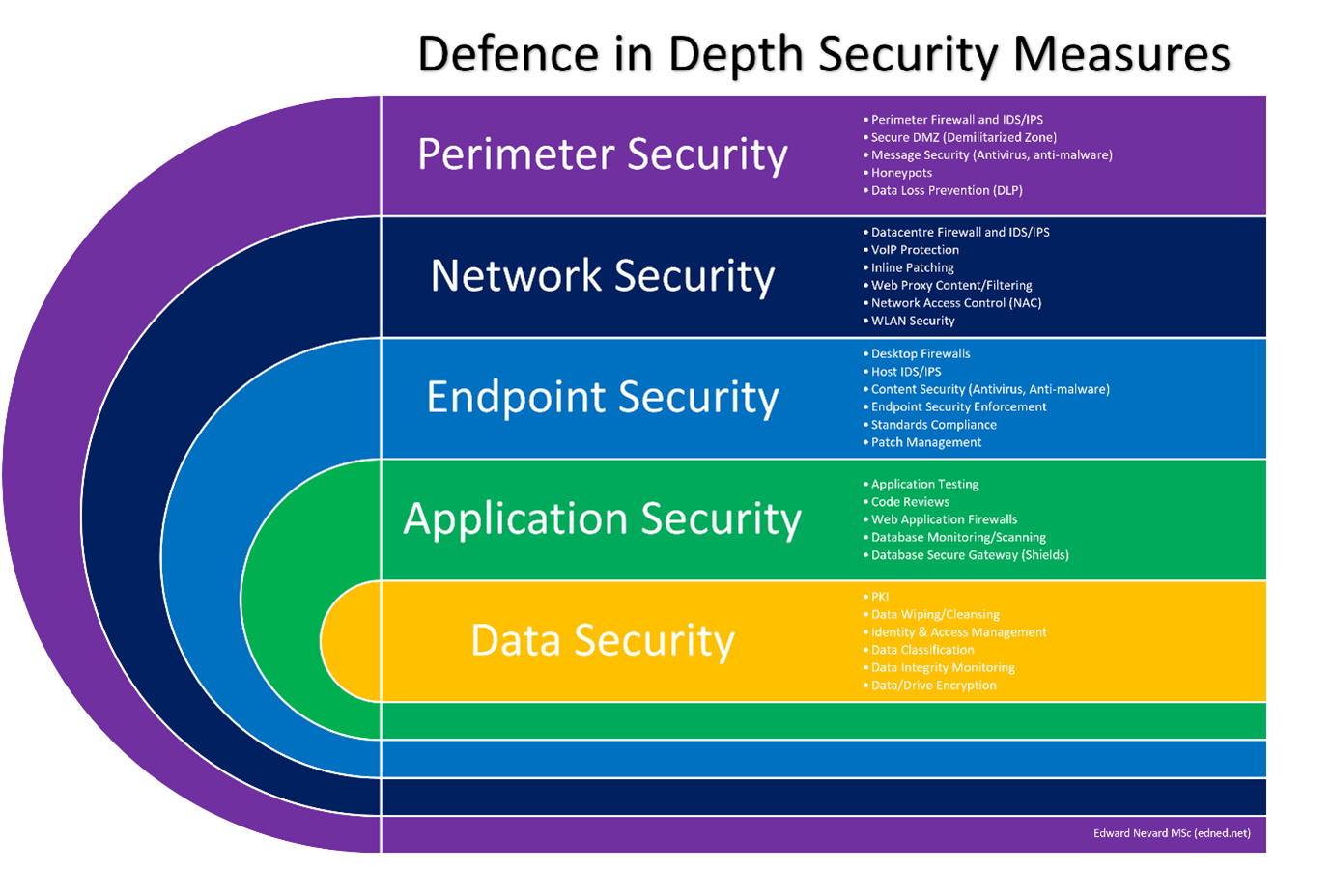
This is a simple defence-in-depth nested diagram that shows the layers of protection that should be typically surrounding your “Mission Critical Assets”, protecting them from exterior threats that will likely occur. I call it the “Defence Onion” Perimeter security is the initial protection layer, which could include defensive methods such as honeypots, permitter firewalls, IDS/IPS systems, etc. Should the bad people get past the perimeter layer, basic network security principles such as WLAN Security, NAC, Web Proxy/filtering, and more, should be used to prevent the attack from being successful from an internal network exploit.
Depending on the environment (for example, public libraries openly allow access to their computers to anyone, universities, etc.), sufficient endpoint security should be implemented to prevent attacks from being carried out. ALL endpoints should have security enabled, no matter what the environment, but additional/different security measures should be implemented for publicly accessible devices. Standards compliance and content security are just a few examples (see Security Measures diagram).
At application layer, especially when outsourcing application development, testing, code reviews, WAFs, database monitoring, and more, should all be implemented to ensure that any security risks within applications are mitigated as much as possible. Finally, the closest layer (and last line of defence) that’s surrounding an organisation/individual’s mission critical assets is Data Security. Practices such as regular data wiping, access management, data classification, integrity monitoring and encryption should all be upheld and maintained to the highest degree.
Even if Harry and Marv get into your network and computer systems, if they’re unable to read or understand the data they were looking for, it’s still a loss for them and a win for you.
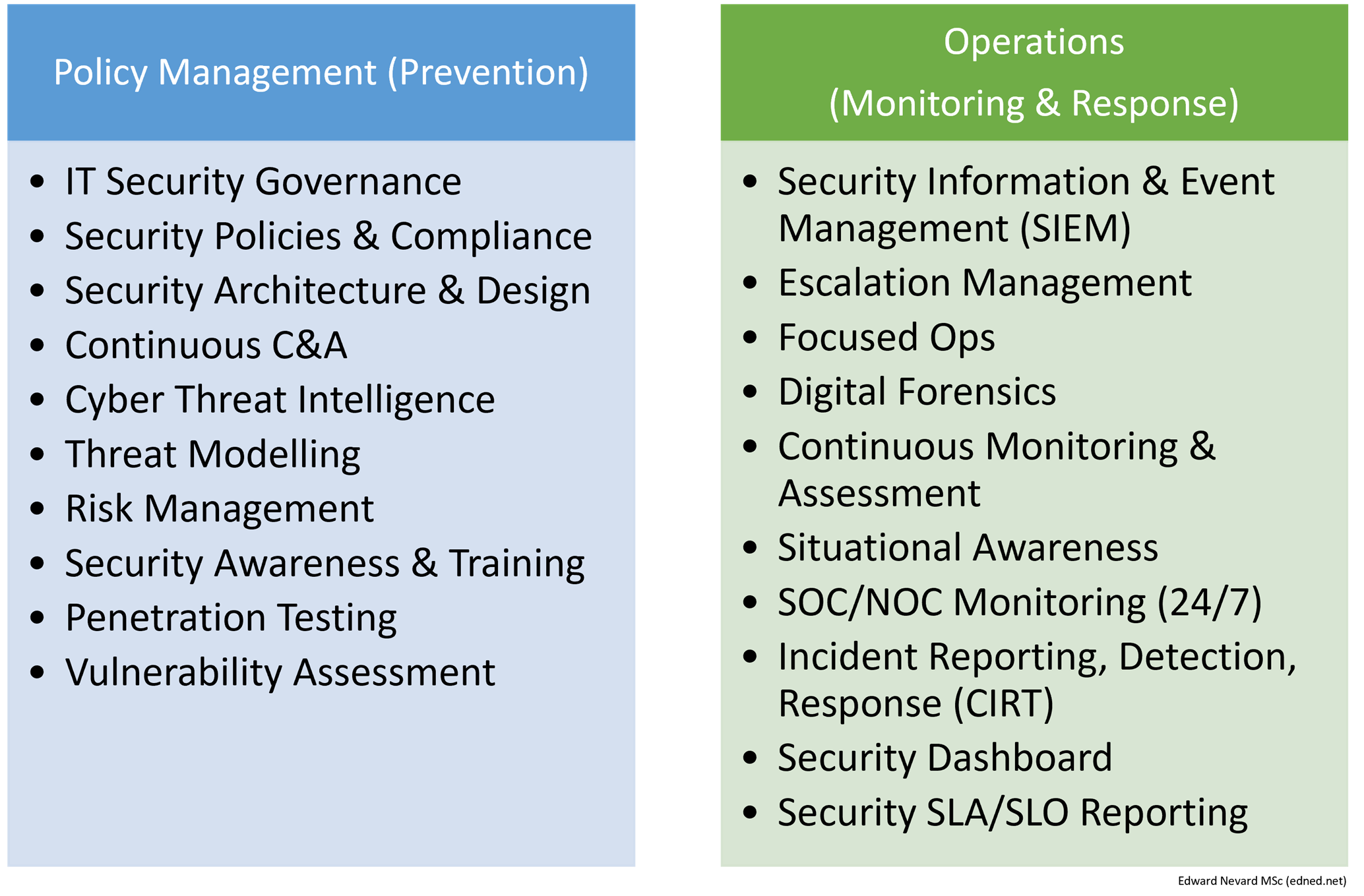
Policy & Operations
To ensure all the above security measures are upheld, there’s two main areas of governance that should be regularly upheld and reviewed within an organisation. These are Policy Management (to prevent an attack in the first place), and Operations (to monitor and respond to attacks). Following all of the bullet points above effectively should minimise and mitigate risks of all types of attacks, both from external and internal threats.
Conclusion
So, if you want to understand Defence in Depth, think of Kevin in Home Alone. He even makes it hard for Harry & Marv to get out once they’re in! In the first movie, the rope to the tree house is a classic example.
This is my way of explaining how cybersecurity professionals can and should think about Defence in Depth. I hope you find it useful, despite being quite a vivid metaphor on the subject!
Stay safe out there!